Built for Tomorrow’s Threats, Today
SentinelOne redefines modern security with self-learning AI defenses, a seamless all-in-one platform, and a history of stopping attacks others miss
The Evolving Risks for Endpoint Security
Machine-Speed Attacks
Ensuring the security of endpoints is vital in today’s cybersecurity landscape. With attacks becoming rapid, increasingly sophisticated, and more challenging to identify, traditional protection systems are falling short. It's time to adopt advanced solutions that can effectively combat these evolving threats.
Siloed Surfaces
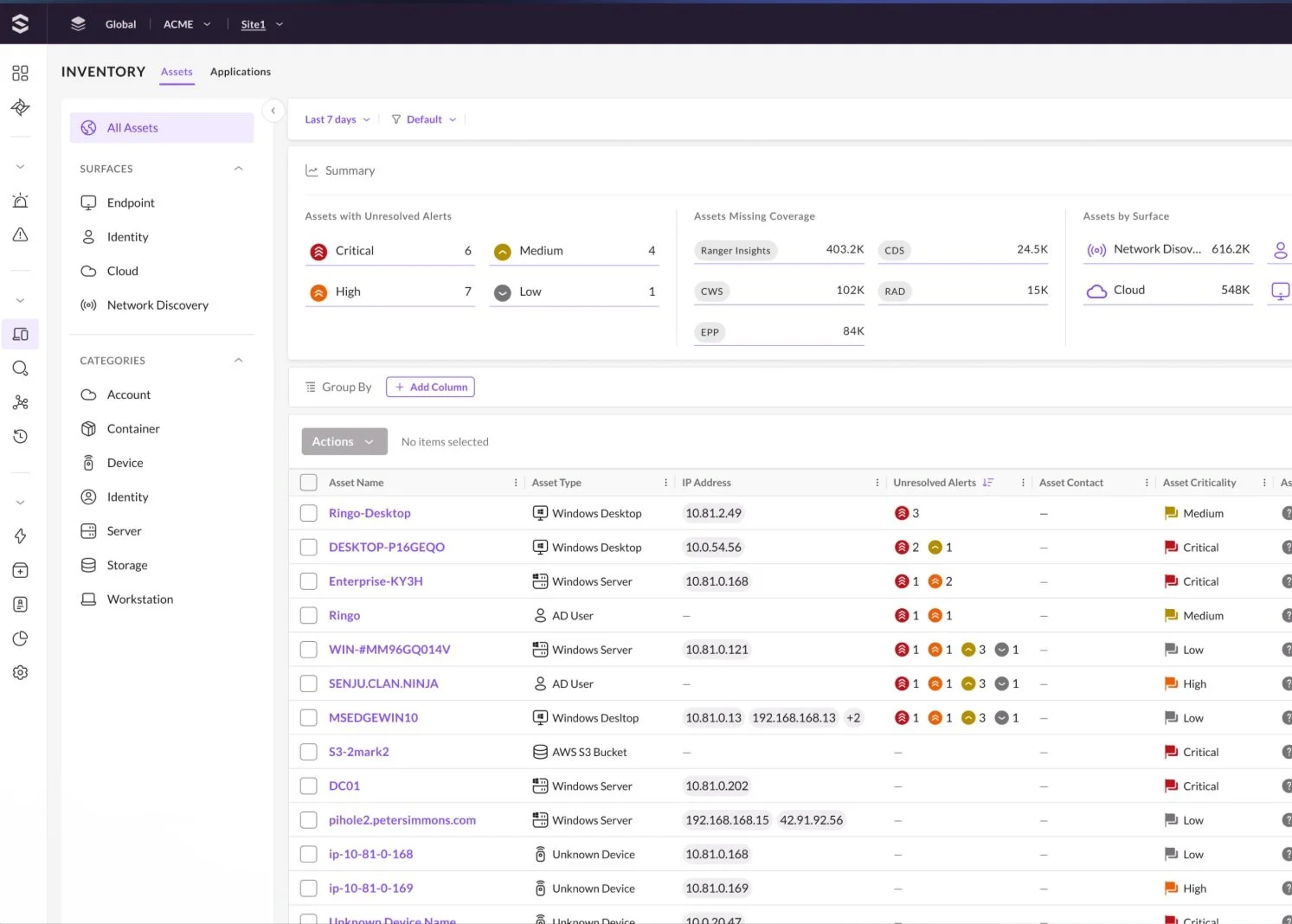
As endpoint and identity attack surfaces have converged, legacy systems frequently lack the ability to provide seamless visibility across devices and the users interacting with them.
Overtaxed Teams
Modern security teams must accomplish more with fewer resources as the scope and complexity of their tasks continue to grow, which increases the necessity for providing analysts with more accessible tools and AI assistance.
Protect against malware with autonomous, machine-speed prevention powered by on-device AI.
Detect ransomware with behavioral and static AI models that analyze anomalous behavior and identify malicious patterns in real-time without human intervention.
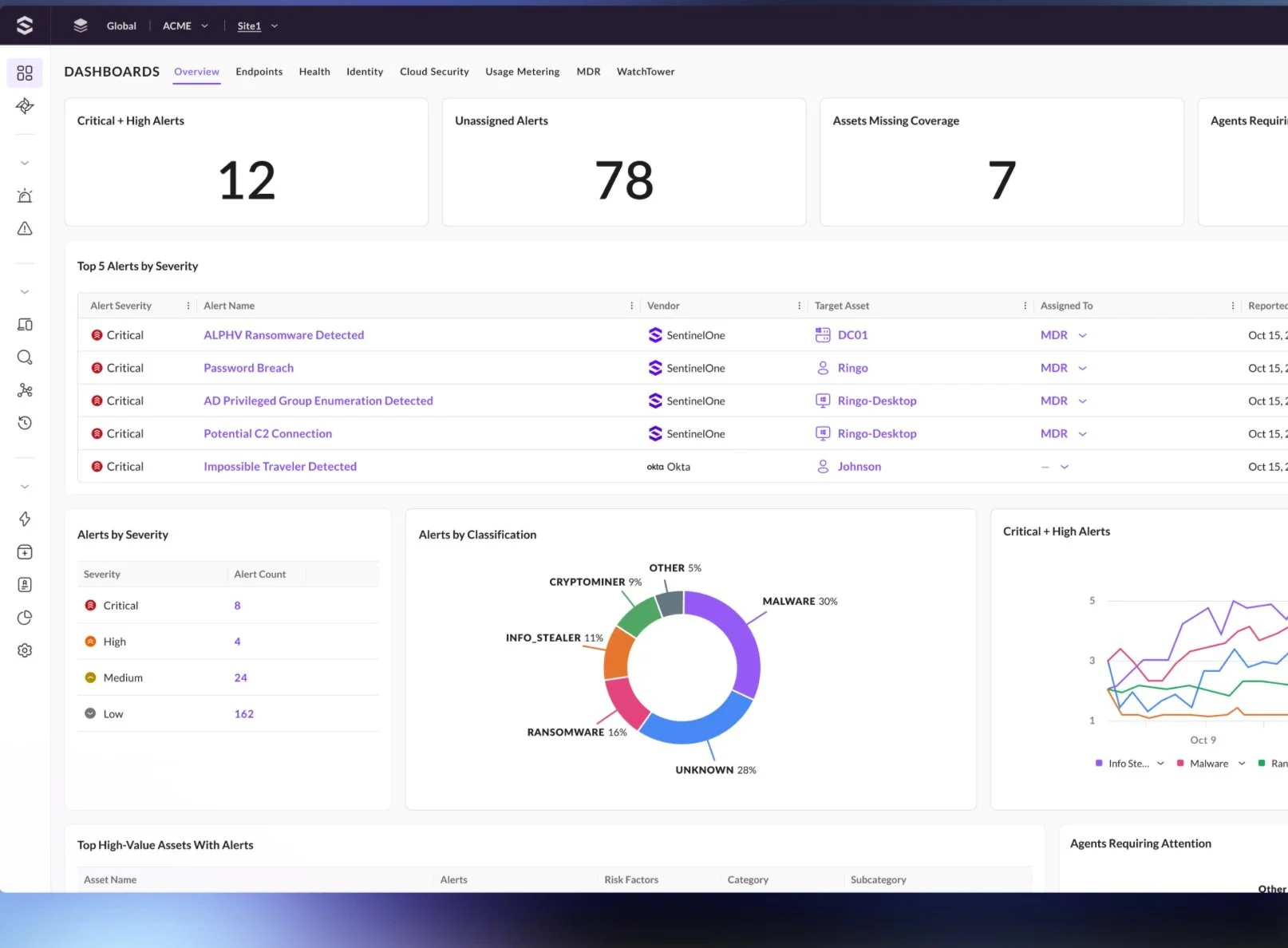
Get critical endpoint and identity alerts with real-time visibility from system-level to identity-based attacks.
Stop Attacks with Unmatched Protection and Detection
Remediate threats with automated or 1-click response/rollback actions.
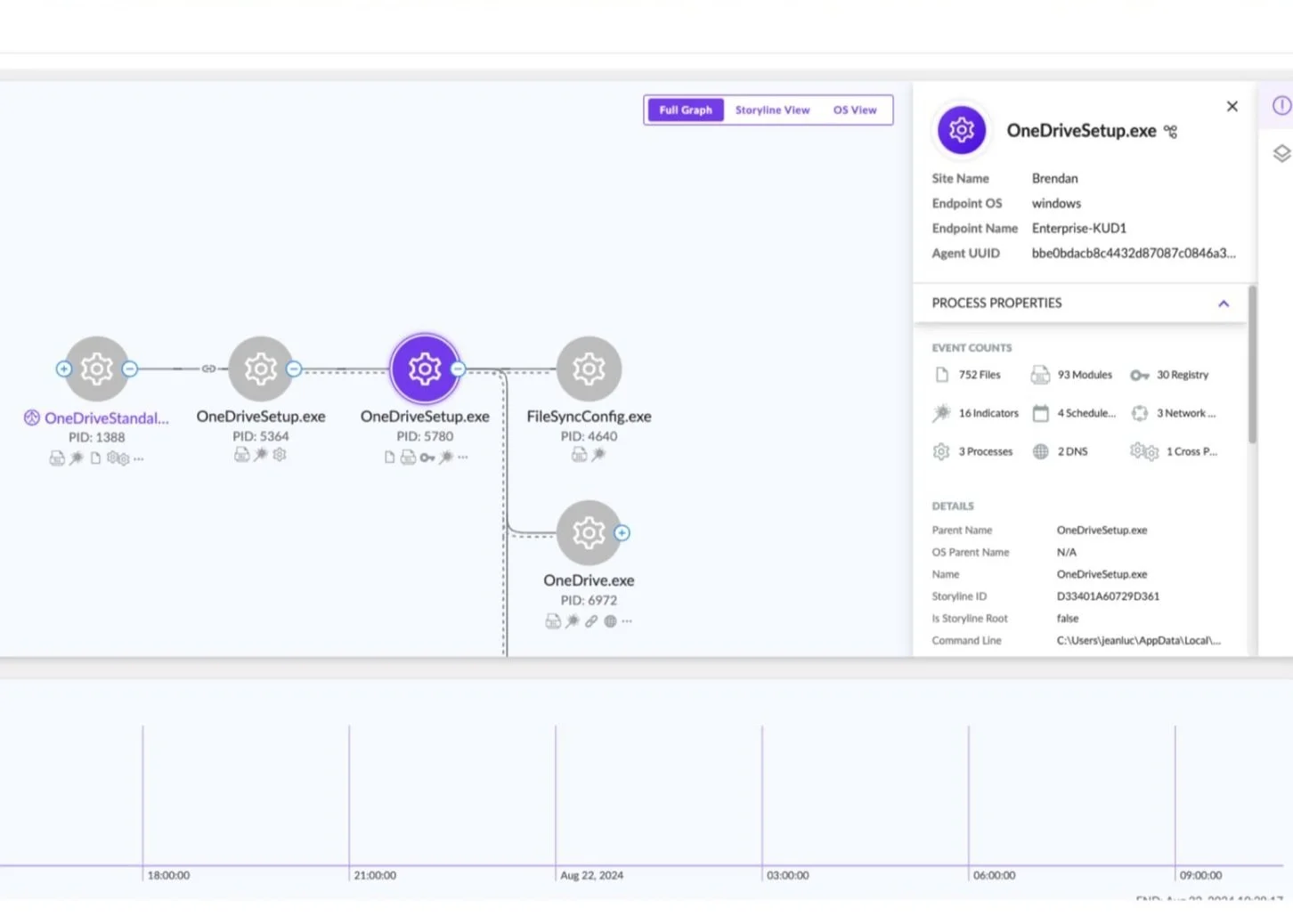
See the full picture of attacks and respond quickly with Storyline®, which automatically links related events and delivers real-time, actionable correlation and context.
Correlate and prioritize alerts across workstations, identities, and exposures.
Minimize Disruption
with Fast Response and Remediation
Gain comprehensive security with an architecture built from the ground up to provide EDR capabilities and identity protection in a single package.
Enjoy industry-leading coverage across Windows, macOS and Linux operating systems.
Leverage a lightweight, autonomous agent designed for minimal user impact and architected to minimize kernel interactions.